Introduction
When two entities (like Alice and Bob) want to communicate securely, they need to ensure that the communication is encrypted, tamper-proof, and authenticated. This tutorial demonstrates how Alice and Bob can communicate securely using a trusted Certificate Authority (CA) to sign their certificates, symmetric encryption for message secrecy, and digital signatures for authenticity and integrity.
In this tutorial, we will walk through the process of setting up secure communication between two parties, Alice and Bob, using OpenSSL. This guide will cover generating keys, creating certificate signing requests (CSRs), signing certificates, and encrypting/decrypting messages.
We will use OpenSSL, a powerful tool for cryptographic operations, to perform each step. Let's break this process down into manageable steps:
1. Generating Private and Public Keys for Alice, Bob, and the CA
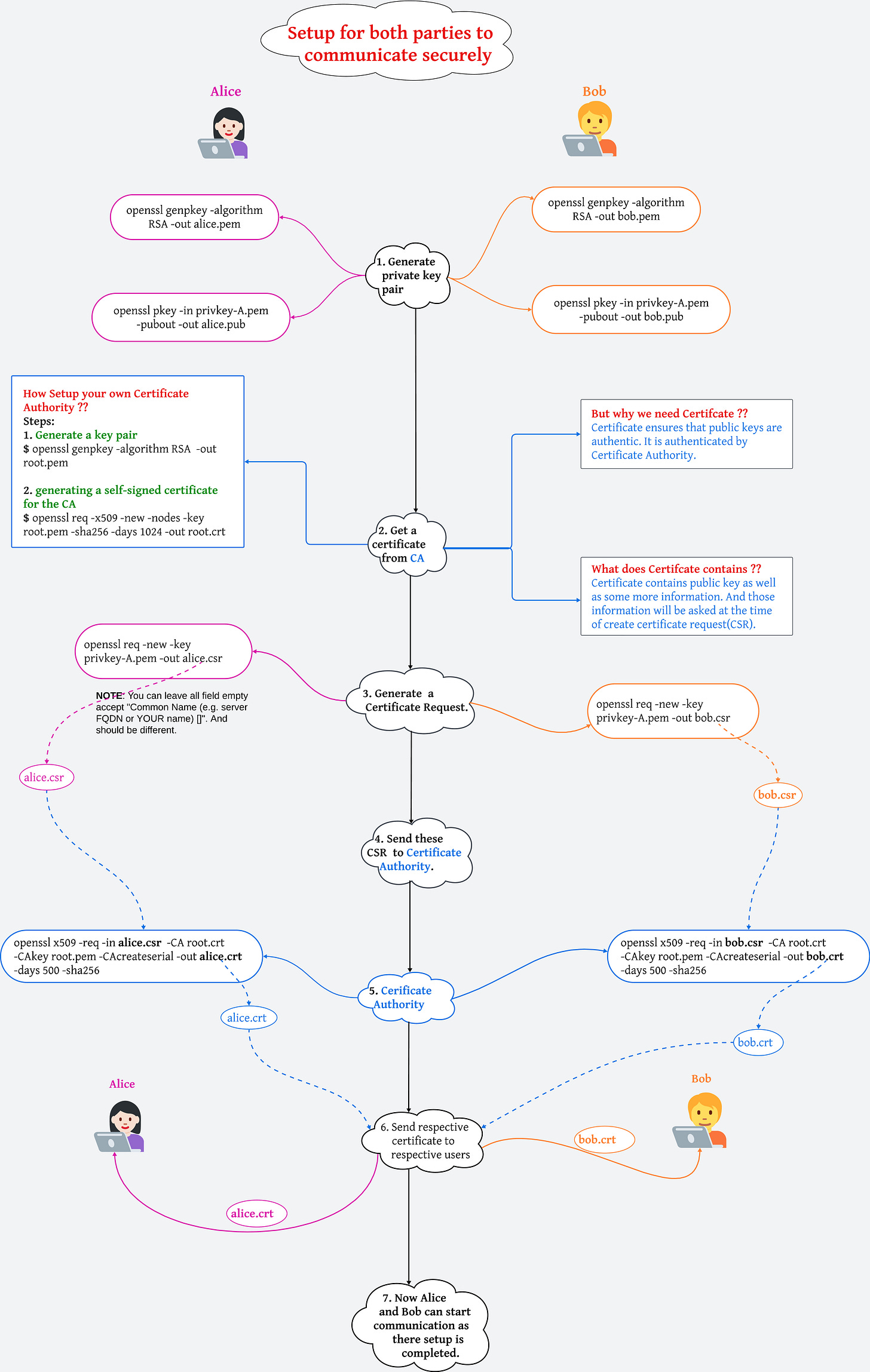
Step 1: Generate a private key for Alice
$ mkdir Alice Bob CA # Create directories for Alice, Bob, and the CA
# generate a private key for Alice
$ openssl genpkey -algorithm RSA -pkeyopt rsa_keygen_bits:2048 -pkeyopt rsa_keygen_pubexp:3 -out privkey-A.pemExplanation: Alice generates her private key using the RSA algorithm with a key size of 2048 bits. The public exponent is set to 3 for simplicity, but typically 65537 is used.
Step 2: Generate a private key for Bob
$ cd ../Bob
# generate a private key for Bob
$ openssl genpkey -algorithm RSA -pkeyopt rsa_keygen_bits:2048 -pkeyopt rsa_keygen_pubexp:3 -out privkey-B.pemExplanation: Bob generates his private key in the same way as Alice did.
Step 3: Generate a private key for the Certificate Authority (CA)
$ cd ../CA
# generate a private key for CA
$ openssl genpkey -algorithm RSA -pkeyopt rsa_keygen_bits:2048 -pkeyopt rsa_keygen_pubexp:3 -out rootkey.pemExplanation: The CA (a trusted third party) generates its private key. The CA will later use this key to sign certificates for Alice and Bob.
2. Retrieving Public Keys from Private Keys
Step 4: Retrieve public keys for Alice, Bob, and the CA
# Alice's public key
$ cd ../Alice
$ openssl pkey -in privkey-A.pem -pubout -out pubkey-A.pem
# Bob's public key
$ cd ../Bob
$ openssl pkey -in privkey-B.pem -pubout -out pubkey-B.pem
# CA's public key
$ cd ../CA
$ openssl pkey -in rootkey.pem -pubout -out rootpubkey.pemExplanation: Public keys are derived from the private keys. These public keys will be shared, while private keys are kept secret.
3. Creating Certificate Signing Requests (CSRs)
Step 5: Create CSRs for Alice and Bob
# Create CSR for Alice
$ cd ../Alice
$ openssl req -new -key privkey-A.pem -out A-req.csr
# Create CSR for Bob
$ cd ../Bob
$ openssl req -new -key privkey-B.pem -out B-req.csrExplanation: Alice and Bob create Certificate Signing Requests (CSRs), which are requests to the CA to sign their public keys, ensuring that they are legitimate. A CSR contains the public key and identity information.
4. CA Signs the CSRs and Issues Certificates
Step 6: Self-sign the CA certificate
# Generate a self-signed certificate for the CA
$ cd ../CA
$ openssl req -x509 -new -nodes -key rootkey.pem -sha256 -days 1024 -out root.crtExplanation: The CA generates a self-signed root certificate, which will be used to verify the certificates it issues for Alice and Bob.
Step 7: CA issues certificates for Alice and Bob
# Sign Alice's CSR
$ openssl x509 -req -in A-req.csr -CA root.crt -CAkey rootkey.pem -CAcreateserial -out A.crt -days 500 -sha256
# Sign Bob's CSR
$ openssl x509 -req -in B-req.csr -CA root.crt -CAkey rootkey.pem -CAcreateserial -out B.crt -days 500 -sha256Explanation: The CA signs Alice's and Bob's CSRs, granting them certificates that are valid for 500 days. These certificates authenticate Alice and Bob by linking their public keys to their identities, verified by the CA's signature.
5. Verifying Certificates and Preparing Public Keys
Step 8: Verify the certificates
$ openssl verify -CAfile root.crt B.crtExplanation: Alice or Bob can verify each other’s certificates by checking them against the CA's root certificate. This ensures that the public key truly belongs to the person it claims to represent.
Step 9: Extract public keys from certificates
$ openssl x509 -pubkey -in B.crt -noout > bob_pubkey.pub
$ openssl x509 -pubkey -in A.crt -noout > alice_pubkey.pub
# Share public keys
$ cp bob_pubkey.pub ../Alice
$ cp alice_pubkey.pub ../BobExplanation: Alice and Bob extract each other’s public keys from the certificates, which will be used for encryption and verification.
6. Secure Symmetric Key Exchange
Step 10: Alice generates a symmetric key
$ cd ../Alice
$ openssl rand -out symkey.pem -base64 32Explanation: Alice generates a random symmetric key. This key will be used to encrypt the actual message using AES (a symmetric encryption algorithm). Symmetric encryption is faster and more efficient for large data.
Step 11: Encrypt the symmetric key for Bob
$ openssl pkeyutl -encrypt -in symkey.pem -pubin -inkey bob_pubkey.pub -out symkey.encExplanation: Alice encrypts the symmetric key using Bob’s public key. Only Bob, with his private key, can decrypt this symmetric key.
Step 12: Alice signs the symmetric key
$ openssl dgst -sha1 -sign privkey-A.pem -out signature.bin symkey.pemExplanation: Alice signs the symmetric key with her private key. This signature ensures that Bob can verify the integrity of the key and confirm it came from Alice.
7. Bob Decrypts and Verifies
Step 13: Bob decrypts the symmetric key
$ cd ../Bob
$ openssl pkeyutl -decrypt -in symkey.enc -inkey privkey-B.pem -out symkey.pemExplanation: Bob decrypts the symmetric key using his private key, making the symmetric key usable for decrypting the actual message.
Step 14: Bob verifies Alice’s signature
$ openssl dgst -sha1 -verify alice_pubkey.pub -signature signature.bin symkey.pemExplanation: Bob verifies the signature using Alice’s public key. This ensures that the symmetric key has not been tampered with and was indeed sent by Alice.
8. Secure Message Transmission
Step 15: Alice encrypts the message
$ cd ../Alice
$ openssl enc -aes-256-cbc -pass file:symkey.pem -p -md sha256 -in message -out ciphertext.binExplanation: Alice encrypts the message using the symmetric key and AES-256-CBC (a secure encryption algorithm). The message is now securely encrypted.
Step 16: Bob decrypts the message
$ cd ../Bob
$ openssl enc -aes-256-cbc -d -pass file:symkey.pem -p -md sha256 -in ciphertext.bin -out messageExplanation: Bob decrypts the message using the same symmetric key. He can now read the original message sent by Alice.
Conclusion
In this tutorial, Alice and Bob used public-key cryptography to exchange a symmetric key securely and encrypted their communication using AES. By using digital signatures, they ensured that the communication was authenticated and untampered. The role of the CA was crucial in verifying Alice's and Bob's identities and providing trust in their public keys.
This process is the foundation for how secure web communication happens, such as in HTTPS, where a browser (client) communicates with a server securely using certificates and encryption.
Resource: link